
With the increase in the competitive environment in the growing IT sector, security is not taken into account in the design and testing phase of the products that are created rapidly. Projects where security processes are not implemented and ignored are caught in the network of hackers. According to research conducted in the US, cybercrime is expected to cost countries and organizations more than $6 trillion by 2021, with security threats increasing exponentially. Companies that face such cyber attacks face financial loss, data damage, business interruption, reputation and customer loss.
To avoid such incidents, software security should be included in projects from the very beginning of design and should be promoted as a business priority. Generally, security remains in the second priority in organizations until a security breach occurs. To deal with this, DevOps, which is applied in IT companies, has started to be replaced by DevSecOps.
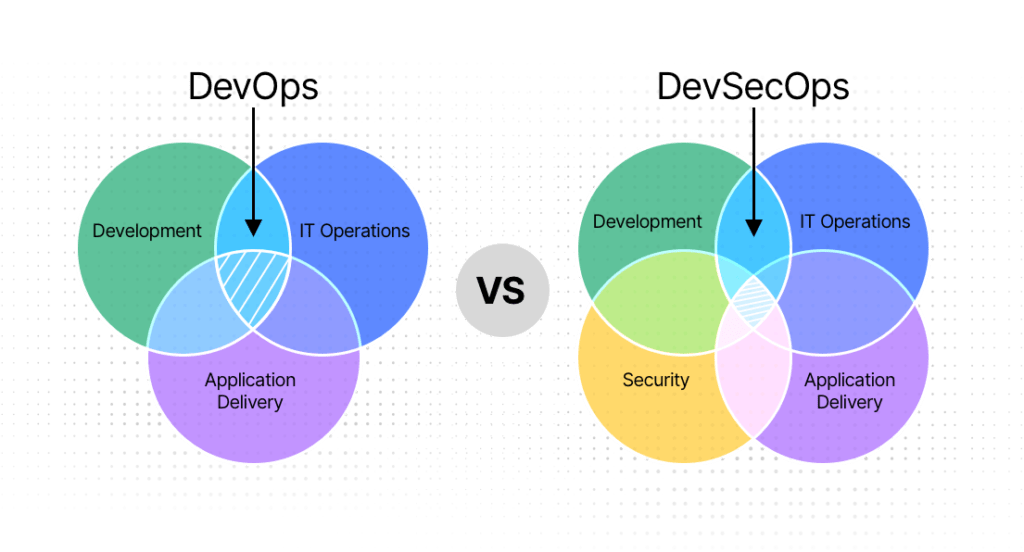
So, What is DevSecOps?
While the DevOps culture in organizations provides companies with a faster, functional and scalable process, security and compliance are often overlooked. Although security processes are normally implemented in DevOps processes, security was often bypassed during the product delivery phase. This means that all versions are released to the customer without security analysis. In fact, in DevOps processes, the fear of missing the deadline is forgotten that ignoring security will bring more risks to projects, and security errors in this process cause serious security vulnerabilities. This is why DevSecOps has emerged. DevSecOps is actually the inclusion of security teams in the DevOps process. DevSecOps aims to take security to the next level by tightening the security processes implemented in the Devops process.
DevSecOps is a set of software principles that emphasizes collaboration, communication and automation between all stakeholders – customers, developers, testers, IT and security teams – at the start of a project to recognize security at the very beginning of the SDLC (Software Development Life Cycle) process, thus minimizing vulnerabilities and applying security to the entire DevOps process. So instead of adding security at the end, DevSecOps makes security a core component of the software development workflow and aims to accelerate software development processes without compromising security.
What happens if we only apply the DevOps process in our projects and do not use the DevSecOps process?
Security breaches are one of the biggest threats governments and organizations face today. Imagine adding malware to an application during the SDLC process and not finding the malware until the application is deployed to the customer, the damage to both the customer and the company’s reputation would be enormous. In application development and deployment, it is essential to distribute security equally across development and operations teams. Once security is integrated into the DevOps process, everyone from the developer to the network administrator will prioritize security. DevSecOps integrates active security audits and penetration testing into agile development. Rather than applying security to the finished application, it aims to apply security to the entire product development process. This allows companies to realize security-focused continuous delivery by implementing the DevSecOps process instead of DevOps. In addition, considering that today’s large projects often include open source code, testing 3rd party software is an important requirement in the DevSecOps process. It is very important for organizations to identify code dependencies and not neglect open source security management.
How do we integrate DevSecOps into DevOps culture?

In order to implement DevSecOps processes in companies, the first step is to plan the process. During the planning phase, acceptance tests, user designs and threat models should be created. For the planning phase
- Jira
- Rally
tools can be used. With planning, security starts before a single line of code is written. Then the most important phase is the information phase, for which Agile and DevSecOps training courses should be provided to employees. After the trainings are completed, companies need to make a comprehensive assessment of the SDLC. Speed is one of the key principles of DevOps. In a continuous integration and continuous deployment (CI/CD) environment, how quickly and accurately code is released to the live environment is of great importance. Therefore, our goal from now on is to integrate automation into the processes. The deployment process should be done in a DevSecOps style. All services in a pipeline should be generated and deployed using automation and IaC (Infrustructure as Code). Subsequent processes start with the tool chosen for the CI server. These tools are
- Jenkins
- Bamboo
- Travis CI
- Microsoft Azure
can be. A successful CI developer discipline ensures that code is integrated into a VCS early and often. You can also check out the blog post about Top 7 Continuous Integration Tools for DevOps
For VCS (Version Control System),
- Git
- Apache Subversion
- Bitbucket
- Github
tools can be used. Then the configuration and testing phase begins. For configuration operations;
- JFrog
- Nexus
- Cmake
- Archiva
- Gradle
- Grunt
- Maven
such tools can be preferred. After the configuration process is completed, 3 main test phases should be applied. These are automated unit tests, performance and integration tests. Each time a new code is committed, the risk of the software application being under attack increases. Therefore, the application code, dependencies, libraries and underlying infrastructure should be re-evaluated. In addition to these reviews, security, static code analysis, penetration tests and vulnerability scanning should be performed using automation tools. To check open source software, dependencies and code quality in projects;
- Dependabot
- Snyk
- Anchor
tools such as the following can be preferred. The first form of automation security testing that should be applied is static code analysis. Static code analysis takes place during the continuous integration (CI) phase in the DevSecOps pipeline. Static code analysis tools integrated with Jenkins and Bamboo (for CI tools);
- SonarQube
- HP Fortify
- SWAMP
- OpenVas
- Checkmarx
- SpotBugs
- SCale
It is not enough to monitor the system only with these tools. The people responsible for security in companies should be tasked with monitoring the reports generated by automation tools that analyze static code. The second form of automation security testing, the implementation of automated penetration of web applications, takes place in the CI phase of the DevSecOps process. A number of penetration testing tools that can be considered by information security teams are listed below.
- OWASP ZAP
- Gauntlt
It should be strategically added to the CI build plan. If projects use containers, Docker images should be automatically scanned, which is the third form of automated security testing. This form of automated security testing is more important than scanning the application code. Automated vulnerability scanning of Docker images requires security and operations (IT) teams to work together. After the integration of these tests is realized, the following automation tools can be integrated into the system for functional and unit tests
- Robot Framework
- Junit
- Pytest
- TestNG
- Mocha
Functional automation and unit tests should be performed with test frameworks. After testing, the deployment and operation process is started in order to perform secure management operations. This is where
- Chef
- Ansible
- Saltstack
- Puppet
such tools may be preferred. Then the monitoring phase begins. Monitoring the DevSecOps process is important. Therefore, automation tools should be preferred for monitoring. The metrics collected in this process are necessary for security and audit tools. These metrics are as follows, for pipeline metrics; deployment, response rate, code quality and program management metrics should be addressed. In addition to these metrics, metrics such as deployment time, deployment frequency, cost of failed deployments, number of failed deployments, percentage of successful tests, attack analysis details should also be collected. Infrastructure metrics should also be collected and monitored. Tools such as Prometheus, Nagios and Datadog can be used for this. Finally, it is necessary to monitor the performance of an application deployed to production and record the resulting metrics. Infrastructure as Code (IaC) provides a version controlled infrastructure and forms the backbone of CI-CD processes. It is one of the processes that should be implemented throughout the DevSecOps process. In addition to establishing environmental equivalence, IaC brings with it a culture of quality. If dockerfile is used for systems, each layer versions to be used in the file should be examined by information security teams. After determining that they are risk-free
- JFrog
- Nexus
can be stored in tools such as Docker. If Docker is used, images downloaded from DockerHub should be vulnerability scanned using tools such as Anchore, Twistlock or Clair. Finally, orchestration tools should also be used in the DevSecOps process. As a tool
- Docker-Compose
- Docker-Swarm
- Kubernetes
- RedHat Openshift
- Rancher
one of these is preferable.
To summarize briefly,
The DecSecOps architecture that companies should implement is as follows.
Planning and Development: Security requirements, secure technologies and threat model,
Configuration: Secure code and configuration, secure solutions,
Testing: Unit and integration testing, functional and non-functional testing, system and quality testing,
Security: Security testing, vulnerability analysis, vulnerability scanning
Deployment and management: Fast and secure deployment, integrated security management,
Enforcement: Ensure secure monitoring, reliable feedback and vulnerability management[8]
The benefits of the DevSecOps process,
- Early identification of vulnerabilities and minimization of vulnerabilities,
- Good collaboration and communication between developer and security teams,
- Enhanced operational efficiency with security across the enterprise
It contributes to the company infrastructure in many ways, such as more speed, agility and rapid response to change needs for security teams.